🌱 PoC Azure FrontDoor
PoC to secure Azure Function behind an Azure FrontDoor, gaining load balancing, DSA and WAF capabilities.
TL/DR
- Gist containing artefacts: https://gist.github.com/myreli/fd37b6f29957c9b9180bed984ae5f1bd
- Total costs R$0.21 on Azure App Service (Due to the serverfarms, all other resources fall into always free services)
Concept
Expose azure apps and functions through a secure FrontDoor instead of direct access (which is insecure) or API Gateway setup (which is a bit more complex, but combining both is a common approach).
Client → Azure FrontDoor → Azure Functions
[File: b5315926-c0ec-43c0-aa3c-99e4eaab82f1]
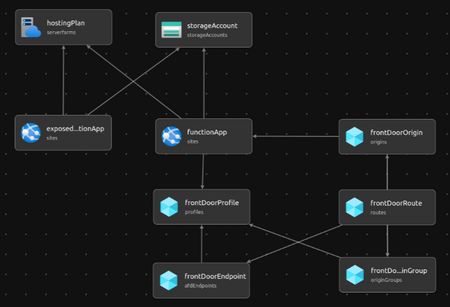
Deployment
Create a resource group and deploy the template:
az group create --name poc-frontdoor --location "East US"
az deployment group create \
--resource-group poc-frontdoor \
--template-file poc.bicep \
--parameters appName=poc
All parameters are optional:
locationdefaults to resourceGroup locationappNamedefaults to auto-generated stringfrontDoorEndpointNamedefaults to auto-generated string
All other resources are deployed using a auto-generated string or its own name, eg:
resource frontDoorOriginGroup 'Microsoft.Cdn/profiles/originGroups'
name: 'frontDoorOriginGroupName'
resource hostingPlan 'Microsoft.Web/serverfarms'
name: 'hpe${uniqueString(resourceGroup().id)}'
Testing
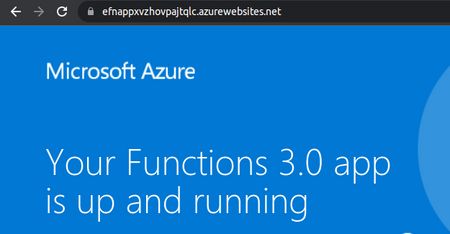
- Access the app without FrontDoor (the demo public function): [File: faf2cd3f-91fd-4e2b-9378-8fc03cd47de8]
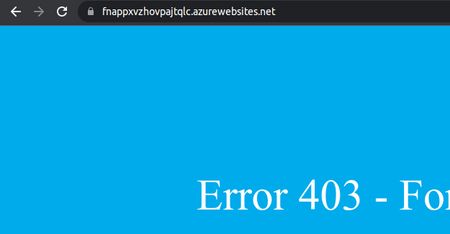
Access the app with FrontDoor (the demo private function): [File: 580d19d6-93b3-40aa-9066-7f263b71eb47]
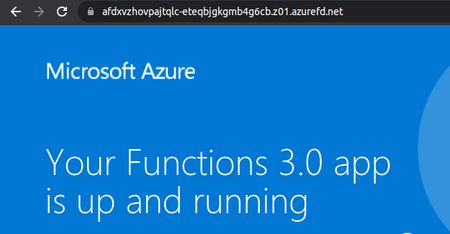
Access the app trough FrontDoor:[File: 7b4b34da-ab56-4b5f-a1a2-fe56eedbe609]
Clean Up
Delete the entire resource group to prevent waste:
az group delete --name poc-frontdoor
Next
- [ ] Restrict access to FrontDoor (eg IP Restrictions)
Resources
🌱 Seedlings são ideias que recém tive e precisam de cultivo, não foram revisadas ou refinadas. O que é isso?